OPC Factory Server 3.63 - Service Pack 2 (including OFS DEMO, LARGE, SMALL and WSP)
Bug fixing : The server may crash when configuring xvm symbol link exported from a Control Expert Safety namespace. Bug fixing : Item Id declared with postfix ;C or ;S used to be in conflict with the same item Id declared without postfix. Thus, the canonical data type of the second added item used to override the canonical data type of the first added item. Bug fixing : A synchronous Read operation performed after a failed synchronous \ asynchronous Write operation used to fail. Vulnerability fixing : Update link to Microsoft Visual C++ 2015-2022 redistributable package. Vulnerability fixing : Update XML parsing by using MSXML6 installed on the computer. MSXML6 security updates must have been applied by the computer administrator. Vulnerability fixing : The configuration tool was exposed to "CWE-611: Improper Restriction of XML External Entity Reference" Vulnerability fixing : The server was exposed to CVE-2021-26414 Windows DCOM Server Security Feature Bypass. It is adapted to take advantage of the deployment of KB5004442 on both OFS and OPC-DA client computers. Note that OPC-DA client must be also adapted. Enhancement : Compatibility with Windows 11 and Windows Server 2022. Enhancement : AddItems OPC DA operation used to be blocked until data dictionary reloading completion It is fixed by updating the item definition on the fly. Note that DDTs and String Arrays accessed globally can not be updated on the fly and item creation will return E_FAIL. Enhancement : Reduction of memory footprint and fragmentation. Enhancement : New license model for driver mode. Enhancement : Update mode support by silent install. It is possible to run silent install to update an OFS version >=3.40
Files
| File Name | ||
|
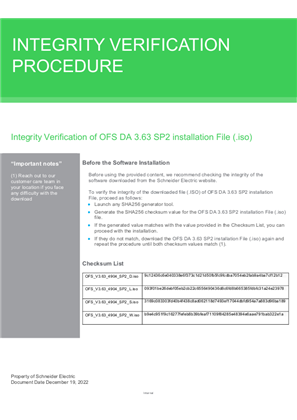
EcoStruxure OFS DA 3.63 SP2 Integrity Verification Procedure.pdf
|
|
|
|
OFS_V3.63_4904_SP2_D.iso
|
|
|
|
OFS_V3.63_4904_SP2_L.iso
|
|
|
|
OFS_V3.63_4904_SP2_S.iso
|
|
|
|
OFS_V3.63_4904_SP2_W.iso
|
|
|
|
contents.html
|
|
Related products
Product Ranges:
-
OPC Factory Server

